Last updated on 9 October 2024
In-house email verification expertise
At Mailnjoy, we have technical expertise in verifying email addresses.
Nowadays, even if it’s easy to find many articles on any subject, especially thanks to the Internet and books, we nevertheless believe that the best person to answer a specific question is someone who has made the subject his speciality, and who will therefore be able to provide factual elements that are more accurate and precise than generalist articles.
So if you want to learn the best tips on “how to make good bread”, the most reliable answer is to ask that question to a good baker who makes hundreds of breads every day and really knows what he’s talking about.
Well, the same goes for “how to verify an email address“: Mailnjoy verifies millions of them every day thanks to its own technical engine, and today we’re going to give you all the details and secrets so you can fully understand how it all works.
In particular, you’ll discover which steps are mandatory to test the validity of an email address, which steps are optional (used by some email verifierAn email verifier, also known as an email checker, is a software used to check an email address or a list of email addre... More only), which specific extensions are proposed by some email checkers only to differentiate from other tools, or why some email addressesEmail addresses, also known as "electronic addresses" or simply "emails", represent a form of digital communication popu... More are “safe”, or why others will always remain “risky” despite our best efforts… in short, lots of tips and concrete facts, which you won’t read anywhere else, so that verifying an email address really has no more secrets for you!
We’ll start our analysis by detailing the most classic steps in email verification (common to all email verification tools), then we’ll go into detail on the specialized steps, offered only by certain higher-quality email checkers.
Basics of email verification
For this point, we invite you to first read the topic how to recognize a reliable email verifier, in order to discover the key elements that any good email verification tool should present. These basics are the necessary foundation for any reliable email verification solution, and will be appended by the technical elements discussed in this article.
Mandatory steps to verify an email address

a) Email address format check
The very first step in verifying an email address is to check that it has a valid format: the SMTPSMTP stands for “Simple Mail Transfer Protocol”. Created in 1982, SMTP is an email transfer protocol used for... More protocol has defined the rules about what can and cannot constitute an email address. These elements are checked by the email verifiers:
* check that the e-mail address contains an “@” character (and not several times this character), which must be both preceded and followed by other characters
* check that the total number of characters in an email address does not go beyond 254 (beyond this limit, the e-mail is not correct)
* the characters after the “@” represent the domain, which must be made up of a non-empty character string, followed by a dot, followed by an extension. If one of these elements is missing or is not in the expected format, then the email will not be correct.
* the characters before the “@” sign represent the “username” part of the email: this must not be of zero size (≥ 1 character).
Note: there is no size limit on the username part (only the email address total size of 254 characters maximum must be respected), but in the real life it is strongly advised to stay below 64 characters. The longer the email address, the more complex it will be to spell it orally to someone, and the greater the risk of making a typographical error, which is why 99% of email addresses created are less than 48 characters long, making them easily “understandable” and readable by a human.
On the opposite, an very long email address will seems obviously strange to you, and anyone can already assume that it’s not normal (and won’t be confident to write on it) when looking at it. For example:
thisadressisanexampleofverylongandcomplexusernamewhichdontreallygivetrustandmotivationtowriteonitbuttechnicallyspeakingitcouldbeavalidemailadressisntitfunny.58742478521@example.com
Indeed, even if this email address is technically correct according to it’s size (and could therefore be a “technically valid” email if the mailbox exists), it’s unlikely that you’d consider it to be trustworthy, is it? 😉
* check that there are no unauthorized characters in the username or domain.
Typically, you’ll regularly come across email addresses that have been spelled with accents (which are not allowed), or character encoding problems in a list of email addresses that have erased some characters and replaced them with a “?”.
The only allowed characters are:
* letters from “a” to “z”
* numbers from “0” to “9”
* the special characters that are allowed: ” . -“, “_”, “+”
Note: contrary to popular belief, the case of an email address has no influence: PIERRE@example.com is the same email address as pierre@EXAMPLE.COM . So there’s no need to check this aspect, and email addresses are often automatically converted to lower case after being verified for easier reading.
b) Check if the domain associated with the email address is able to receive emails
Even if the email address format is correct, this does not mean that we can yet consider the email address to be valid. The second mandatory step is to determine whether the receiving domain is able of receiving emails (in a general way, on any existing mailbox).
To do this, we’re going to look at a domain-specific DNS field called the MX (Mail Exchanger). If this DNS record is non-existent or misconfigured, then the domain will not be able to receive any email, and we can conclude that the email address checked is necessarily invalid.
Example with domain “gmail.com”, for which the MX value is valid:
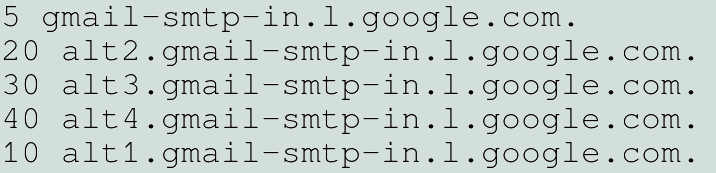
Sometimes, some domains do have an entry defined in their MX field, but it’s an incorrect configuration that doesn’t accept any email.
If someone asks to verify an email address on one of these faulty domains at this moment, the email verification tool will indicate that the email is invalid (and rightly so) because the domain doesn’t allow any email to be received. If the administrator of the faulty domain discovers and corrects the problem shortly afterwards, the email address will once again be usable and routable.
This explains why some emails are considered invalid by an email verification tool, and then suddently the same email address starts working again shortly afterwards.
As the email verifier takes a “snapshot” at a given moment of which email addresses are working and which are not, this “snapshot” proves to be accurate at that precise moment: the more time passes and the more changes are made to the various domains, the less representative this analysis will be of reality.
c) Verify current email status
Now that we’ve verified both the email address format, and the fact that the receiving domain is able of receive emails (in general), it’s time to check whether the email address precisely requested actually exists.
To carry out this verification, we use a direct connection to the SMTP server of the domain concerned (some refer to this step as “pinging the email address”). This is the KEY step in order to find the status of the email address, and represents the basis of email verification techniques.
In practical terms, we’re launching a connection request to the email box, with the same commands (in SMTP language) as a webmail client (e.g. gmail) would use to send an email to a recipient. The main difference is that here the commands are sent as lines of code (in order to scan the remote server’s response lines) and that SMTP communication is spontaneously stopped before the “send command” is given.
With this technique it is possible to get the mailbox status without having sent any real email (this is essential for an email verifier, which, it cannot be stressed enough, must NOT send any email to the addresses tested)
Example of communication to check the SMTP status of an email address :

The complexity of this step lies in being able to correctly interpret the technical code returned by the remote server, and thus to accurately determine whether the remote server is indicating that the email exists or not.
In theory, these response codes are standardized (and should therefore be easy to recognize), but in the real life we soon realize that many servers do not follow these standards, and send back response codes that are sometimes even inverted! (for example, indicating that the mailbox is valid, when in fact it is invalid, or the opposite).
This situation implies that you need map countless SMTP servers around the world and recognize their own response codes… Failure to do so will result in a high rate of false positives or false negatives, taking away all the benefits from the email address verification process.
It should also be noted that checking the SMTP status of an invalid email address is equivalent to having generated a hard bounceA hard bounce is an email marketing concept. It refers to a notification which indicates that a message sent has not bee... More (for the receiving domain concerned). The important point to understand here is that the email verifier tool will therefore have the same difficulties and possible blockages of its domains and sending IPs as any advertiser who has sent too many invalid emails, and will then find itself blocked in its verification actions.
The creation of an email verifier tool therefore requires the implementation of a sufficiently complex and resilient architecture to be able to continue verifying email addresses even in the presence of a large number of invalid emails every day.
Note: an interesting historical fact to note is that when it was created, the SMTP protocol defined a specific directive enabling an email address to be verified without sending an email to it: this was the VRFY (sender verify) command. However, having to deal with an increasing spam issues, where some malicious actors send a maximum number of emails with unwanted content, almost all SMTP servers worldwide have voluntarily deactivated this function, making it impossible to obtain the status of an email address through this directive (even though it was designed for this purpose in the beginning).
Specific case of catchall emails
Some domains have a special operating mode enabled that makes the previous SMTP connection step unusable: these are so-called “catchall” domains.
These domains have an SMTP server configured so that it accepts ALL incoming emails, regardless of the username part.
So, on these specific domains, if for example you send a message to the following emails, they will all be accepted by the server and will not generate a hard bounce:
stone @ CATCHALL-DOMAIN.COM
fakeemail @ CATCHALL-DOMAIN.COM
contact @ CATCHALL-DOMAIN.COM
thisisabademail @ CATCHALL-DOMAIN.COM
This technical specificity means that on this type of domain, it will not be possible to “easily” determine whether an email address exists or not. Indeed, just because there is no bounce generated when an email is sent, this does not mean that the address checked truly exists, and even less that the emails that might be sent to it will be actually read by someone.
In addition, a number of these domains are even more complex to check, as some are in fact “false-catchalls”: they behave like a catchall domain during the SMTP phase, but can still generate a hard bounce when an email is ACTUALLY sent.
So, there is a double risk in using an email classified as “catchall”: a risk of lower engagement (i.e. sending to an email box that will not be read by anyone) and a risk of hard bounce (if it is a “false-catchall” domain)
This is why emails which belongs to the catchall category are often risky to use. In order to reduce this risk and make it more acceptable to users, high-quality email verifier are gradually implementing innovative solutions, which we’ll discuss later.
Possible additional steps in email address verification

Now that we’ve completed the mandatory steps for verifying an email address (which, overall, classify emails into 3 categories: SAFE / RISKY / UNSAFE), we’re going to list here the additional steps used by some of the best-quality email verifier, which bring more accuracy into the classification process:
Inbox full detection :
This step allows us to determine which email addresses are technically valid but have exceeded their maximum storage quota. They will generate a “soft bounce” if an email is sent to them, and some of them may even become later a type of marketing trap known as “recycled spamtrap”.
Detection of disabled email :
Some emails are technically valid, but their owners have not logged in for too long (or have had an abnormal behavior), resulting in their temporary deactivation. These boxes will make a soft or hard bounce depending on the requested domains, and even if they can be reactivated at any moment, they must be considered as invalid at the present time.
Classification of role-type email address :
This step makes it possible to distinguish and sub-classify valid “function” emails from valid “individual” emails. This enables users to send role-based emails and individuals emails differently, as the engagement rates and related risks are different between these two types of emails (despite the fact that they are both technically valid).
Analysis of the domain creation date :
This step verify the creation date of the domain hosting the email address, in order to adjust the trust of the checked email according to this result.
Indeed, a recently created domain will tend to be more suspect than a long-established one, as many spammers buy and use new domains every day to send large quantities of unwanted emails.
Verification of blacklist membership :
Some email verifiers can also detect whether an email address has recently been used in a spam or phishing email campaign, and can identify this aspect during email verification.
Although this step can be useful, in reality spammers and hackers change email addresses very quickly, which makes it relatively difficult to keep blacklists up to date in real time. Nevertheless, this step can make it possible to avoid sending emails to these bogus email addresses, which would not be of any commercial interest to use anyway.
False-catchall domain detection :
As we saw earlier, domains identified as catchall are sometimes “false-catchall” and can lead to a significant hard bounce rate if these emails are used. Some email verifiers can determine which catchall domains are most at risk (and give a bounce rate estimation on these one) to help customers make the right choice according to their sending strategy.
At Mailnjoy, we offer this specific classification of fake-catchall domains, which are called “protected emails” on our email verifier.
Cross-check validation of catchall emails:
In order to reduce the risk of catchall emails (and false catchall), some email verifiers use cross-checks with other tools (internal or external) to certify some email addresses of these statuses. These cross-checks often enable an additional percentage of email addresses to be certified with a good level of confidence (< 5% bounce), thereby reducing the risk of using email catchalls by targeting only those that have been certified.
Please note that these cross-checks remain theoretical (without any email being sent), which means that it is impossible to have 100% reliability on these addresses (in reality, with a good email verifier, we’re talking about 95% reliability on these cross-checks).
Catchall email validation with true email sending:
Because of the risky nature of catchall emails, some unscrupulous email verifiers have specialized in this technical niche of catchall email verification, by implementing a validation technique that is normally totally banned from the operating principle: the actual sending of an email to the tested mailboxes.
This method, which violates all the rules of good practices and the laws of various countries, is often very expensive (and takes a long time to process), but can provide a greater confidence in detecting emails that are truly valid on these catchall domains.
Even if we mention how they work, so that the reader knows that they exist, we absolutely do not recommend this type of solution, which is not legal in itself, generates nuisance, and puts the people who use them at legal risk.
Differentiate a technically valid email address from a real person

The previous steps have made it possible to classify email addresses, with varying degrees of accuracy and reliability, depending on the email verifier used.
The following steps, which are only carried out by good quality email verifiers, go beyond simple technical validation, and can help identify email addresses that may not be truly associated with a human.
These email addresses are generally of low marketing value, and have lower engagement metrics than those that may have been associated with a real person.
The following analyses can be offered by some email verification tools to go beyond the technical criteria seen above:
Username reliability checking :
The aim here is to recognize suspicious patterns in email addresses, by taking a closer look at the username part. If a suspicious keyword appears or if the format seems abnormally constructed, then it’s possible to indicate that the email address is suspicious despite the fact that, technically speaking, it passed the SMTP connection test.
For example, if these three email addresses were technically valid, would you still think they could be used in your email marketingEmail marketing, also known as Emailing, is a digital marketing strategy that uses email as its medium. It is one of the... More campaign?
noreply @ example.com
spam @ example.com
l.e.m.o.i.p.e.p.u.j.o.p.i.p.a.k.o.i.b.i.r.o.p.t.y @ example.com
Here, it is obvious that these emails are not to be trusted and should not be used, as you would take higher risk to damage your own reputation.
Disposable email detection :
So-called “disposable” emails are emails belonging to specific domains that offer temporary email creation services.
The aim of these services is to provide an email address that appears to be technically “valid”, so that it can be used by a person to sign-up on a website and gain the benefits associated with registration (time limited free usage of the service, free credits, free white paper, etc.), without the person having to give their real email address to do so.
These services, that boast about privacy and spam prevention for their users’ own email addresses, make it easy for bad people to multiply registrations on sites to abuse free services.
Usually benefiting from a very short lifespan (a few minutes to a few hours), these email addresses are then abandoned by their users and pollute companies’ email lists.
As new disposable email services are created every day, and as they regularly change the domains used to send their emails, their detection requires a high level of expertise from email verifiers in order to be able to recognize them correctly.
Autogenerated email detection :
In the same way as disposable emails, some bad users create multiple email addresses on free public ESPs (like gmail, outlook, yahoo, aol, etc.) with the aim of abusing a service without paying for it , then abandon these mailboxes shortly afterwards.
Email address verification tools can therefore offer to detect and classify valid emails in a sub-category of “autogenerated” emails for the ones which display suspicious attributes.
For example, the following emails (if technically valid) could quite easily be classified in this category by a good email verifier:
l.e.m.o.i.p.e.p.u.j.o.p.i.p.a.k.o.i.b.i.r.o.p.t.y @ outlook.com
james123456789@ gmail.com
xwbntgzwaploikjgtfrvbn@ aol.com
Marketing spam or spamtrap email detection :
Detecting spamtrap is a complex analysis, due to the multiple and difficult-to-identify nature of such emails.
Most email verifiers are able to detect some types of spamtrap (mainly typographical spamtrap or recycled spamtrap), but they can hardly detect all those present on a given email listAn email list, also known as an email address list, or even mailing list, is a set of contact email addresses that an en... More.
It is therefore advisable to be cautious about false claims made by some email checkers to detect all spamtrap, which in reality are more often marketing arguments than a true ability to perform this action.
Cross-referencing and cross-analyses :
To go beyond the technical validity of an email address, another possibility is to look at the connections it may have with other platforms. Data cross-analysis, for example, can reveal whether an email address is associated with one or more social networks, or even one or more e-commerce platforms, video platforms, etc.
The presence of an email in one or more specific categories can help to determine whether the address belongs to a person, thus increasing confidence in its commercial value.
Look at last open value or the last click value of an email :
Thanks to partnership with various email routersAn email router is an online service that simplifies and enriches (through statistics and tracking) the email marketing ... More, some email verification tools have recently been able to provide informations on the “last open” or “last click” date associated with a specific email address.
Although this data is subjective (as it relates to a specific router which only has its own personal view on opens and clicks), this metric can also help gain confidence in the email addresses tested.
However, the reliability of this new technique must be balanced against the fact that even bots can easily open or click on links, and so these metrics in no way rule out the possible presence of a bot on an email address with a recent open or click date.
Behavioral attributes of email addresses
Among the criteria used by email routers to determine whether a list of email contacts presents a risk (and whether it should be rejected or blocked when a customer uploads it onto their platform), we find both technical criteria and more subjective criteria linked to behavioral aspects.
So a list in which the contacts are all valid (technically speaking), and therefore presenting only a very low risk of hard bounce, can sometimes be rejected by an email router for no apparent reason. This situation is often misunderstood by customers who don’t understand why this particular list, which is of good quality, is not accepted by a router (notably Sendinblue / Brevo router, which is quite sensitive on that point), but will be accepted and routed correctly by a competing router.
The explanation lies in factors internal to each router, through the history of behavior that these email addresses have had up to now.
If, for example, there are enough email addresses in your list that the router has already tried to send an email to X times before, and their open/click rate is below the median threshold for conventional email addresses, then the router may consider that the contacts provided are not of good quality and freely decide not to accept this list.
Similarly, if the contacts on this list contain several emails on which the router has so far observed an excessively high complaint rate (in comparison with the average for other email addresses), the router may decide that these contacts could be detrimental to it, and prefer to block the list import by indicating that it is not of good quality.
Unlike the technical elements of email validation, these are far more subjective criteria, as the email addresses are all technically valid.
To overcome this type of blockage, some email verifiers also offer to carry out a “behavioral” level of verification through partnerships with email routers.
Mailnjoy offers this specific analysis on request for those who continue to have persistent blockages of their email lists with a router, despite a technical clean-up previously carried out.
Can you create your own email verification tool ?
A question we’re often asked is: “Is it really that difficult to make our own email address verification tool?”.
Well, to answer that question, I’d say that nothing is impossible for anyone who’s willing to really put in the time and has the motivation!
Building an email address verification tool is therefore entirely feasible, but it will all depend on the amount of time and resources you’re willing to allocate to the project. As you will have seen from this article, it will also very much depend on the level of reliability and accuracy you want to have on your email verifier, and the volume of emails you need to check every day.
If your interest is only an internal need for your own company (which processes data on a daily basis), then you’ll probably be better off using an already existing tool specialized in email address verification, as the total cost will be much lower.
If, on the other hand, you want to become a new player in the Emailing ecosystem and offer an email verification service to your own customers, then the article you’ve just read should have given you a significant source of useful technical information to get you started.
Depending on the level of accuracy / granularity of the planned email verifier, and whether you choose to build your own technical engine (or use the engine of another white-label solution), the time and effort required to build your email verifier can vary greatly.
In any case, keep in mind that emailing takes time to grasp the concepts, and that like any other profession, it’s only with time and persistent commitment that you’ll achieve your goals.
Synthesis about how to verify an email address
This article is now drawing to a close, and I hope it will have allowed the more curious among you (if you have come this far, that means you are!) to really understand the different layers behind email verification, and thus to demystify the concept somewhat.
There’s nothing magical about email verification, it’s a profession, an expertise that can be learned and honed with time and passion. So I hope I’ve passed on a little of that passion for a job well done that we have at Mailnjoy, and our daily commitment to helping people who work in emailing to do so with joy and pleasure. Because not only can emailing be fun and enjoyable, as long as you understand the concepts behind it and know how to use it in the right way, it’s also highly profitable, and will probably remain a wonderful communication and marketing channel for a long time to come.
And as always, don’t hesitate to contact us if you’d like to talk to our technical teams or benefit from our expertise to verify your email addresses.

Renaud is an expert in email deliverability.
Here he provides you with a number of files and technical tips to make emailing your business!
